Setting up a Domain Name System (DNS) on Windows Server involves installing the DNS Server Role. This tutorial will walk you through the DNS installation and configuration process in Windows Server 2012.
Microsoft Windows Server 2012 is a powerful server operating system capable of many different roles and functions. However, to prevent overloading production servers with features and options that are never used, Windows Server provides a modular approach in which the administrator manually installs the services needed. To setup and configure DNS, one must install the DNS Server Role on Windows Server 2012. Check out: More Windows Administration Tutorials.
Install DNS Server Role in Server 2012
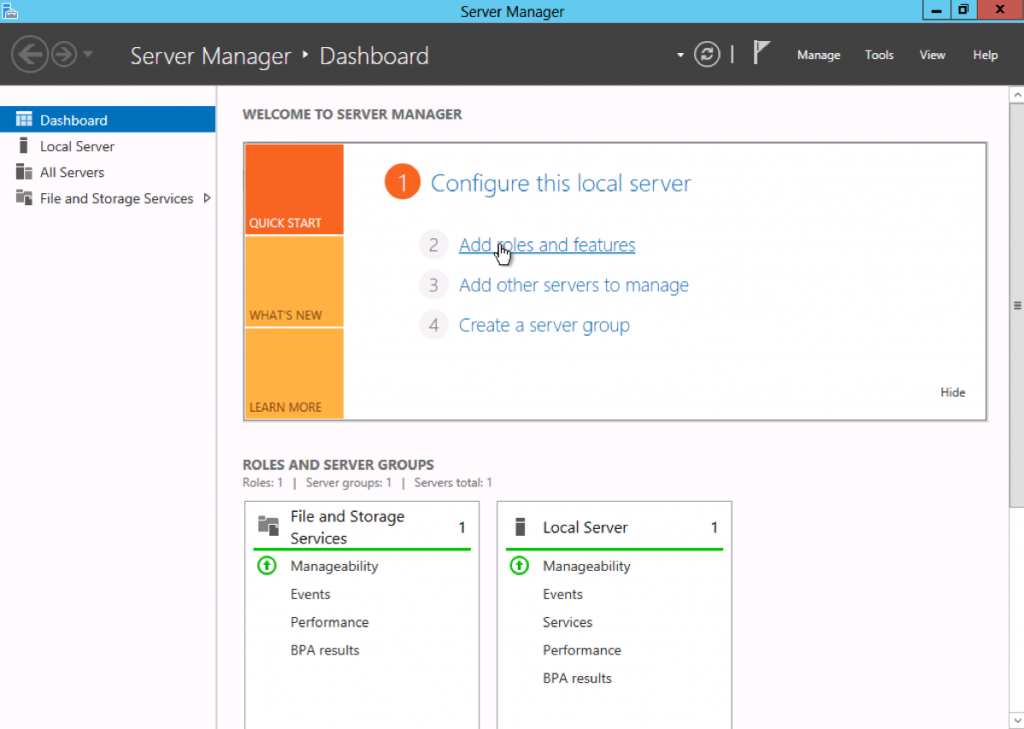
To add a new role to Windows Server 2012, you use Server Manager. Start Server Manager, click the Manage menu, and then select Add Roles and Features.
Click Next on the Add Roles and Features Wizard Before you begin window that pops up. (If you checked Skip this page by default sometime in the past, that page will, of course, not appear.)
Now, it’s time to select the installation type. For DNS servers, you will be selecting the Role-based or feature-based installation.
Next, you will choose which server you want to install the DNS server role on from the server pool. Select the server you want, and click next.
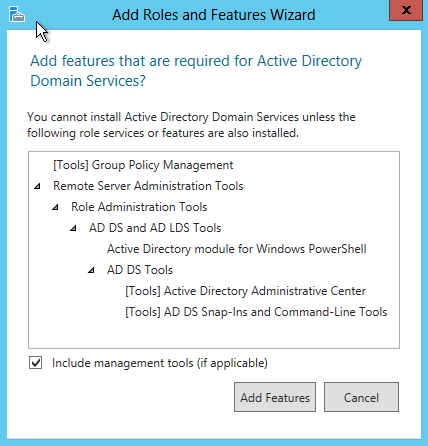
At this point, you will see a pop-up window informing you that some additional tools are required to manage the DNS Server. These tools do not necessarily have to be installed on the same server you are installing the DNS role on. If your organization only does remote administration, you do not have to install the DNS Server Tools.
However, in a crunch you may find yourself sitting at the server console or remotely using the console and needing to manage the DNS Server directly. In this case, you will wish you had the tools installed locally. Unless your company policy forbids it, it is typically prudent to install the management tools on the server where the DNS will be housed.
Now you should see the Features window. No need to make any changes here; just click Next.
Next is an informational window about DNS Server and what it does, although one would assume that if you’ve gotten this far, you are already aware of what it is. Click Next to move on.
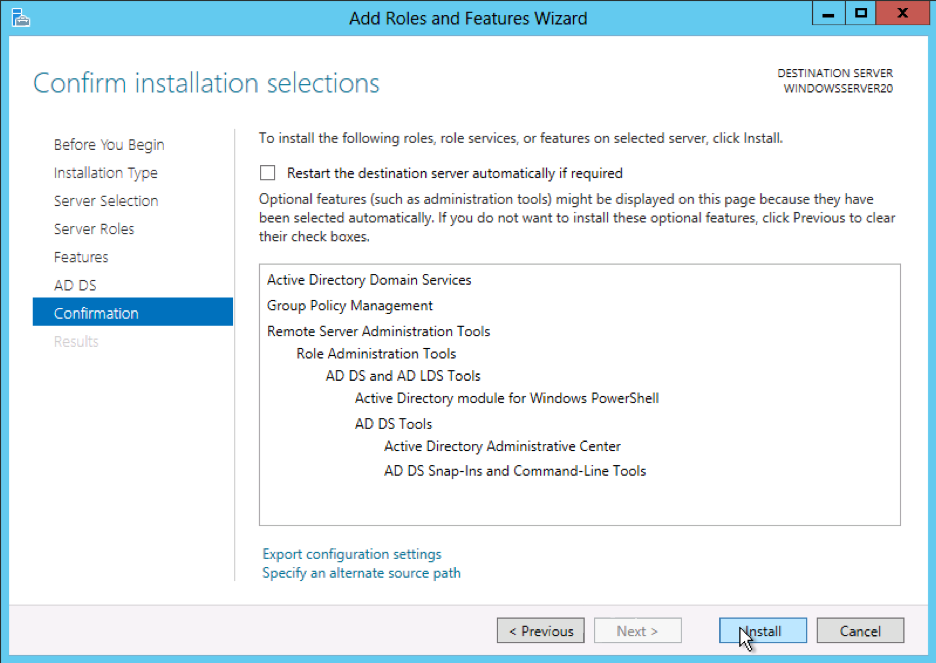
This is the final confirmation screen before installation completes. You can check the box to Restart the destination server automatically, if you like. Installing the DNS Server does not require a restart, but unless you’ve planned for the downtime, keep that box unchecked, just in case.
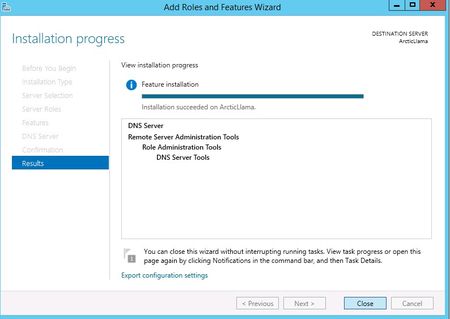
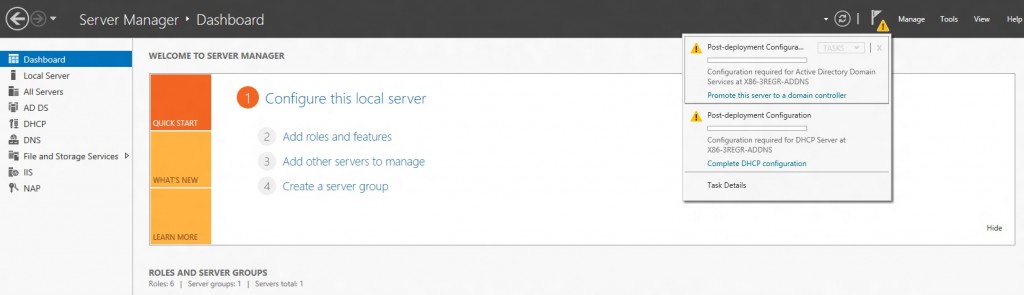
The DNS Server role should now be installed on your server. There should be a new DNS Role tile in your Server Manager.
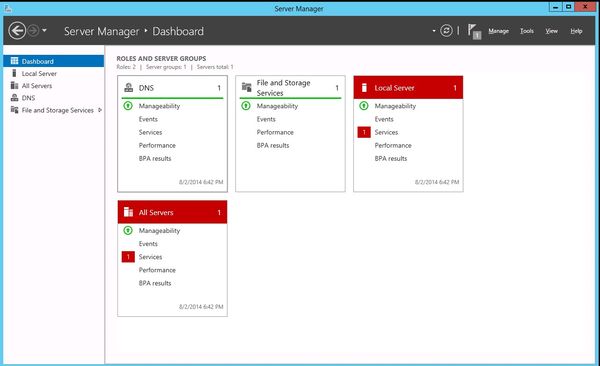
Configure DNS Server in Server 2012
If you are an old pro with DNS server files, Windows Server 2012 does let you edit the files directly. However, Microsoft recommends that you use the interface tools to avoid errors, especially if you are integrating DNS with Active Directory.
If you want to use the command line to configure your DNS, use the dnscmd command. For those of us who don’t memorize TechNet for fun, a few clicks is all it takes.
Within Server Manager, to configure the DNS Server, click the Tools menu and select DNS. This brings up the DNS Manager window.
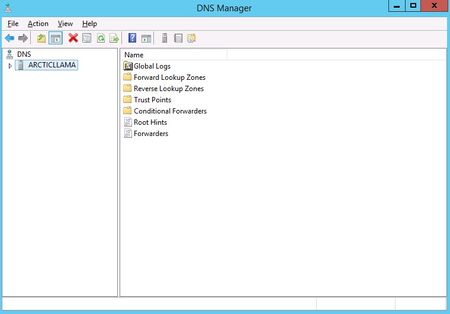
We need to configure how the DNS server will work before adding any actual records. Select the DNS server to manage, then click the Action menu, and select Configure a DNS Server. This brings up the Configure a DNS Server wizard.
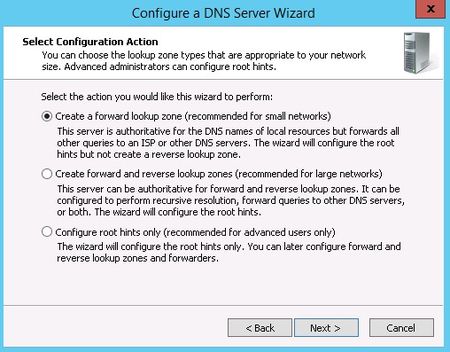
There are three options here. You can either: configure a forward lookup zone only, create forward and reverse lookup zone, or configure root hints only.
A forward lookup zone allows you to do the standard DNS function of taking a name and resolving it into an IP address.
A reverse lookup zone allows you to do the opposite, taking an IP address and finding its name. For example, if a user is set up to print to a printer with an IP address of 10.20.12.114, but you need to know what name that printer goes by so you can find it, a reverse lookup can help. (“Ah, hah! It’s you Third Floor Vending Room Printer #1. Why you give me so much trouble?)
Root hints only will not create a database of name records for lookups, but rather will just have the IP addresses of other DNS servers where records can be found. If you already have DNS setup on your network, you’ll probably want to continue using the same configuration you already have. If not, use forward and backward for most situations. (Backup zones typically don’t hurt anything, and they are nice to have when the need arises.)
After you’ve made your section, click Next.
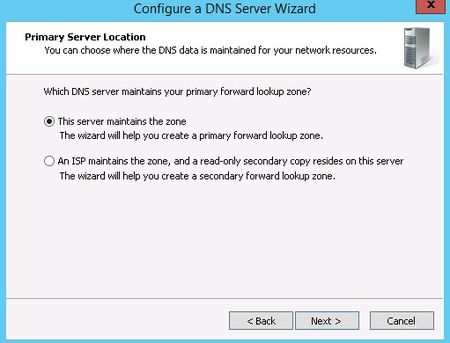
Now, you choose whether this server will maintain the zone, or if this server will have a read-only copy of the DNS records from another server.
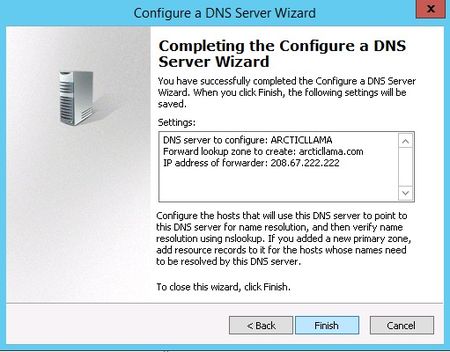
Next enter your zone name. If this is your first DNS server, then this needs to be the root zone name for your entire organization. For example, my zone name might be arcticllama.com. If however, this server will be authoritative only for a subset, and other DNS servers will be responsible for other zones, then the name will need to reflect that. For example, us.arcticllama.com would be the zone name for just the American part of my vast corporate empire 🙂 Click next when you have entered the name.
Now, you need to choose the file name where the DNS records will be stored. The default filename is to add a .dns extension to the name of the zone you chose in the previous window. Unless you have a corporate policy stating otherwise, stick with the convention to make things easier on yourself down the line.
Next you select how this server will respond to Dynamic Updates. Although there are three choices here, only two should actually be used in production. Select the first option to allow only secure dynamic updates if you are integrating your DNS with Active Directory. Select do not allow dynamic updates if your DNS is not integrated with Active Directory and you don’t want to allow dynamic updates. Do not allow unsecured dynamic updates unless you really know what you are doing and have a very good reason for doing so.
Up next is the option to configure forwarders. If your DNS server ever gets a query for which it has no record, it can forward that request on to another DNS server to see if it has the answer
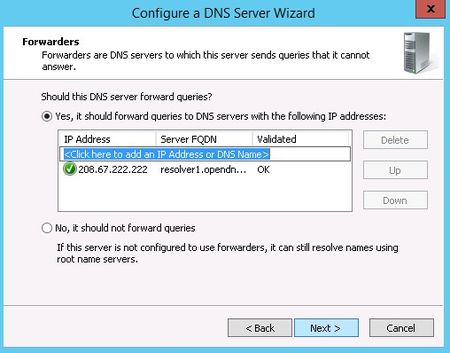
For example, in order to provide name resolution for internet connectivity, you can input your ISP name servers here, or use a DNS provider such as OpenDNS. You can (and should) have more than one server listed in case a DNS server is unreachable for some reason. The order forwarders are listed in is the order they are tried, so place your faster and most reliable forwarder at the top of the list.
Click Next and your DNS server is now configured and ready for use.